It has been a few months since I wrote about the farm in the conservation area. The town has not publicly acknowledged the severity of the problem nor do they have a good plan to address the issues. Town politics has never been an interest of mine, but in order to help nature, I find myself trying to get involved.
Malcolm Gladwell gives a good talk about Generation Z. He spoke about the games of basketball and soccer. In basketball he argued it is a strong-linked sport, meaning you are only as good as your best player. In that sport a single really great player can make all the difference. On the other hand, soccer is a weak-linked sport; the team is only as good as its weakest link. In soccer, the ball often is passed to many players before it is scored. If a single player fumbles, the goal can not be scored. If you want to improve your team it is good to understand what type of game you are playing. Malcolm argued that in our complex modern world, we need to be playing a weak-linked game, but our systems are setup for strong-linked hierarchal leadership. Right now, our town is setup as strong-linked, while it really needs to focus on its weak-linked players. For example, DPW workers who blow leaves into streams, or half-ass fill pot holes and don’t compact them. Or the people who forgot to test the new DPW site for asbestos before taking it via eminent domain. In some neighborhoods, the trash is not being picked up on time this year. Town folks are receiving notices that the water contains certain chemicals above the EPA’s minimum level for good health. What about our town meeting voting system? The society that has been built over the last 100 years is complex and has many moving parts. It is wrong to assume things in our town are working properly. To solve issues in this complex world, it takes a diverse skill set of people to listen closely to each other.
It is funny when Fox News or CNN talks about election security. The state/national election system is probably okay? But how could one know for sure? There is no real concrete data or proof. If I told my 9th grade geometry teacher at LHS that this triangle is probably congruent, instead of using the Side-Angle-Side Theorem, I would get a bad grade. Nationally, a similar standard should apply to voting systems – it should be without a doubt secure and everyone can validate that claim. The system is “probably okay” due to issues attacking such a messy non-standard decentralized system at scale. That being said, in close elections, specific exploitation could yield huge results for downsized risk. The National Conference Of State Legislatures page here describes the system very well. In Longmeadow, instead of county wide administration, our town clerk is in charge of local polling. Please note the election voting system is completely different from the town meeting system, the later of which is examined in this post. As for town meeting, the town clerk is also responsible for recording “all votes passed at town meetings held during his term of office” (General Law – Part I, Title VII, Chapter 41, Section 15).
Just how we have assumed our town officials are keeping our conservation area safe, we have assumed they are keeping our town meeting voting system secure. Both of these assumptions are wrong. At my first town meeting this fall, I was handed a voting keypad branded Meridia EZ-VOTE. This post will describe how our town meeting voting system really works, but also how it is extremely insecure. How can we ensure our conservation area is protected with a vulnerable town meeting?
Town Meeting Voting System
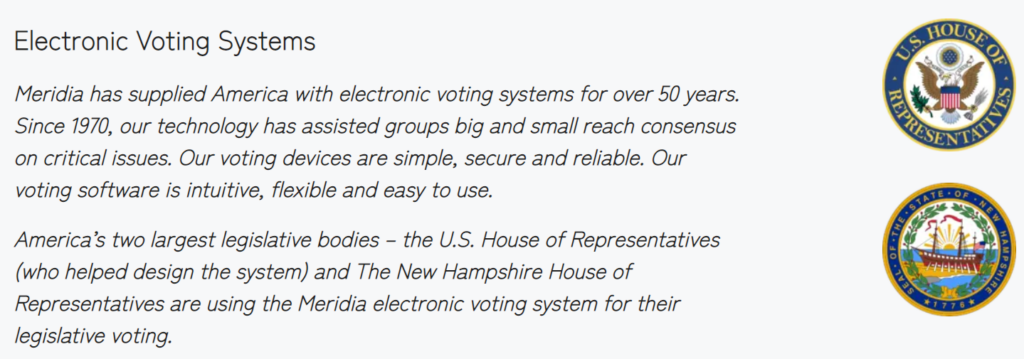
Longmeadow formed the “Electronic Voting Task Force” in early 2021 to “investigate the feasibility, security, costs, and outcomes of electronic voting technology and processes.” On December 31st of 2021, the taskforce recommended to the town clerk that the town of Longmeadow should purchase the Meridia Electronic Voting System. The report can be found on the town website. Interestingly, the taskforce members discuss security and even give an odd description of encryption. In 2022, the voting system was implemented and used at town meeting.
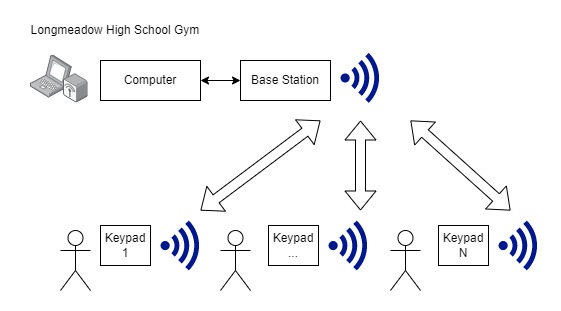
During a polling session, the base station will send wireless messages asking for votes. If the keypad has a vote waiting to be sent, it will respond to the base station with the appropriate selection done by the voter (yes, no, abstain). The base station will send a message back acknowledging the vote.
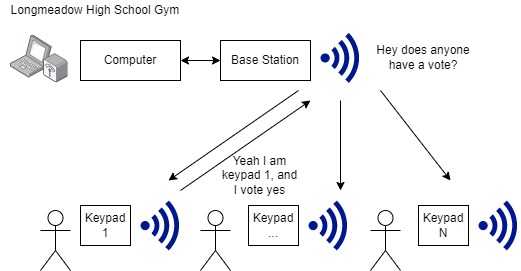
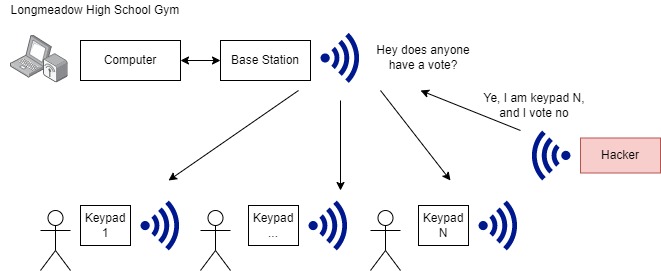
So why is this system insecure? The simple answer is because there is no security. An attacker can send their own messages and spoof the vote. There are no authenticity checks or encryption, there are only integrity checks on transmitted data, which is a standard for radio communications due to noise and interference; but this provides no security.
Meridia
Meridia Interactive Solutions is company from Pennsylvania who sells Audience Response Systems (ARS). Meridia buys all their hardware from a Chinese company named Changsha SunVote Limited. Meridia has SunVote re-brand the hardware to EZ-VOTE, and then they advertise these voting systems to towns, corporations, and presenters. Meridia has also developed software called CloudVOTE and the desktop application EZ-VOTE Connect to interact with SunVote’s hardware.
Apart from being completely and outrageously expensive, Meridia advertises their EZ-VOTE hardware as being secure.
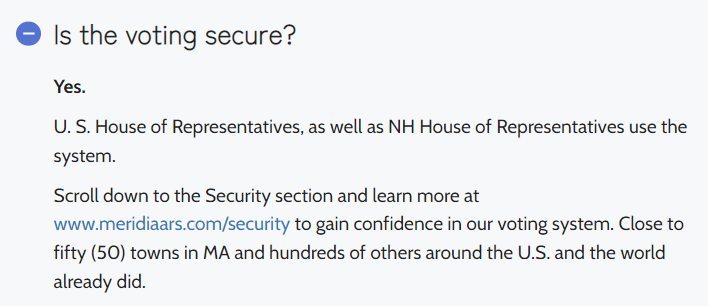
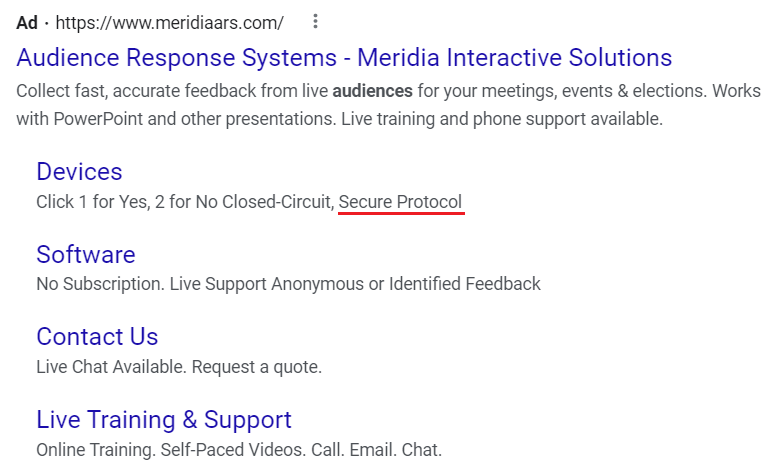
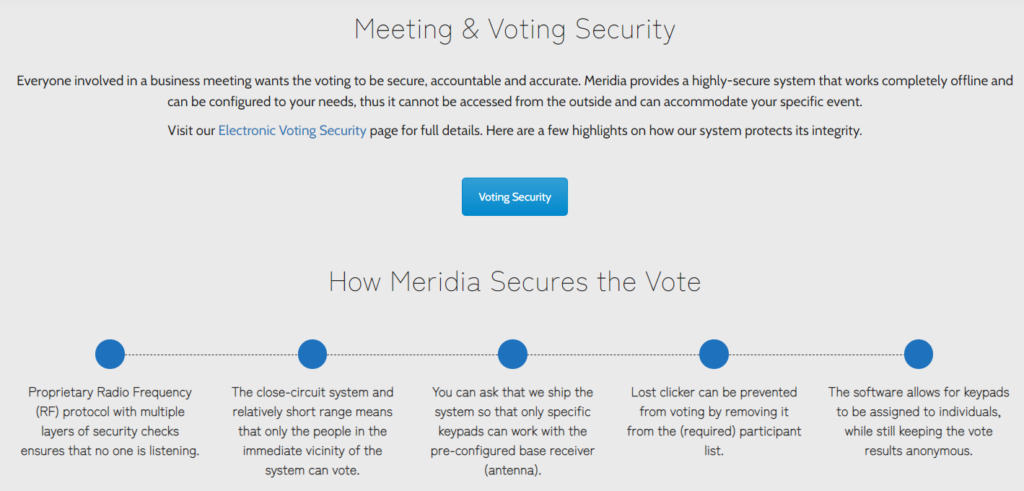

Meridia provides a PDF document for people looking to understand the security better (here).
- Signal Layer Modulation is a term made up by Meridia for commercial purposes. In terms of security, SLM doesn’t ensure anything.
- This doesn’t mean anything for security. An attacker can just use the same “unique” parameters, as they are easily discoverable from radio communications.
- That is good for the attacker.
- SunVote may have had a translating error here, Length of Address Code? This is a 16-bit number and provides no security. Also you cannot just change the signal modulation variables without potentially redoing FCC certification or fundamentally changing the way SunVote devices communicate, the current radio configuration is set by SunVote for specific reasons.
- None of this is a form of encryption. Acceptable forms of encryption are those approved by real cryptographers and NIST.
- First, the protocol is dead simple. Second, CRC is for integrity, it definitely does not “increase the difficulty of interpreting and forging signals.”
- Not a good argument. Plus, there are amplifier and directional antennas available.
Can we safely say this document has been made up to serve the purpose of reassuring non-technical folk that the system is secure?
In the next section, the technical specifics will be explored; Meridia has nothing to do with the actual security because the hardware and embedded software is developed by SunVote.
SunVote
This appears to be a good company. Their website is plain, straight forward, and easy to understand. They do not make false claims and they provide friendly customer support. SunVote is not the issue, the issue is we are relying on their system for secure voting. I did not purchase anything from SunVote, all equipment used in this analysis was purcahsed from Meridia. All SunVote tools and software work with Meridia devices because there is no difference other than branding.

Discovery
Initially, no enclosures for the EA1000 or M30 were opened. Standard software from Meridia and SunVote was used to evaluate the devices. During polling, a Software Defined Radio (SDR) was used to receiver wireless communications. A combination of opensource software and a simple python script was used to receive and decode the communication packets.
The FCC compliance test report for the SunVote M30 keypad shows the frequencies and channels.
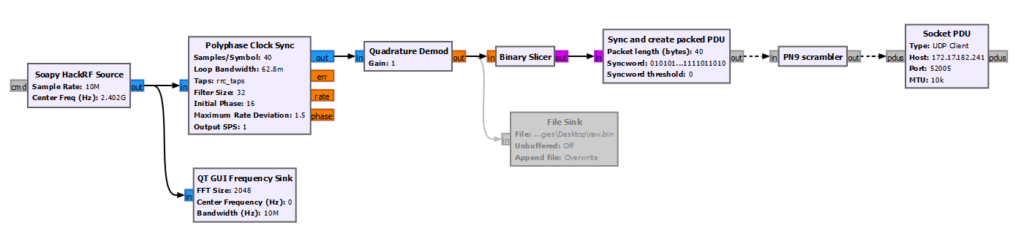
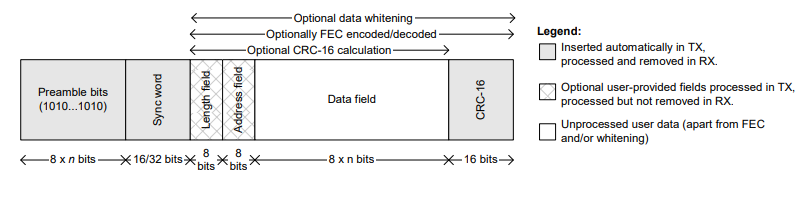
After playing around for bit, I was able to discover that the device uses Minimum Shift Keying (MSK) modulation. The radio is configured to use 0xAAAAAAAA as a 32-bit preamble and 0xA425A425 as a 32-bit sync word. Although for some reason the radio inverts all the data when using MSK, so to distinguish a packet 0x55555555 is used as the preamble and 0x5BDA5BDA as the sync word. The baud rate is 250k. The data field after the preamble, sync, and length is scrambled using PN9. There is a 16-bit CRC after the data field for checking data integrity.
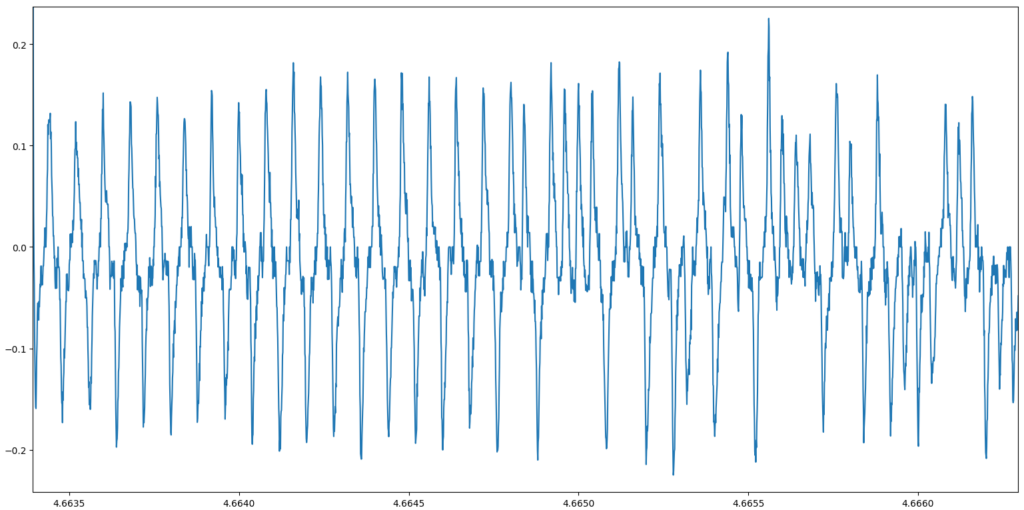
It is possible to use the SDR to conduct replay attacks. This is when radio data is received, stored as raw waveforms, and then retransmitted. The devices are vulnerable to simple replay attacks, such as recording vote packets and retransmitting them later. In order to construct your own vote packets from scratch, an MSK modulator must be used.
EA1000
The EA1000 has a few main parts: AT91SAM7X256 microcontroller, CC2500 radio, CC2591 radio amplifier, and an EEPROM.
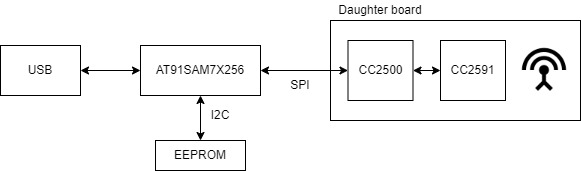
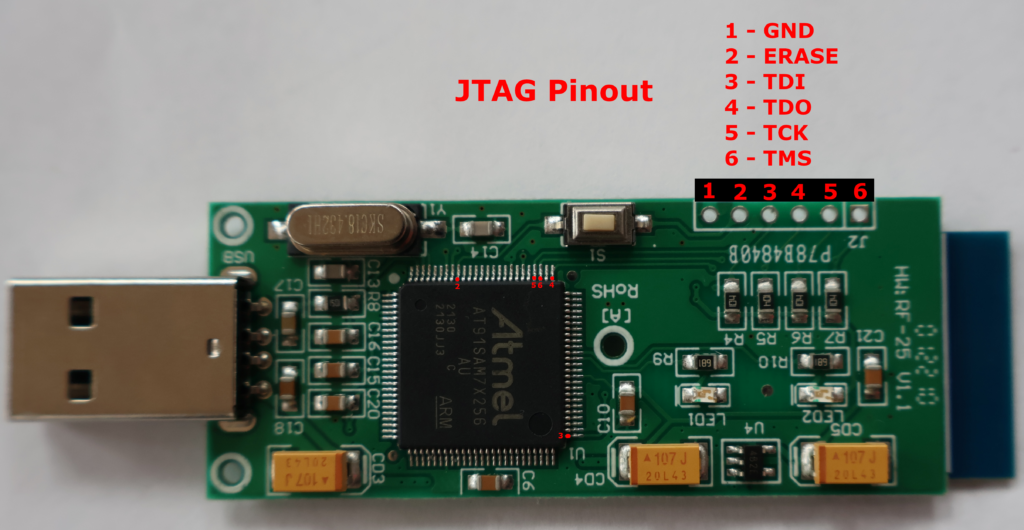
The firmware for the AT91SAM7X256 microcontroller can be dumped using a JTAG emulator. There are no protections to prevent reading this code or debugging the chip using JTAG. The microcontroller firmware was reverse engineered using Ghidra, which is an open source disassembler and decompiler released by the National Security Agency. This confirmed there are no security features to prevent spoofing votes.
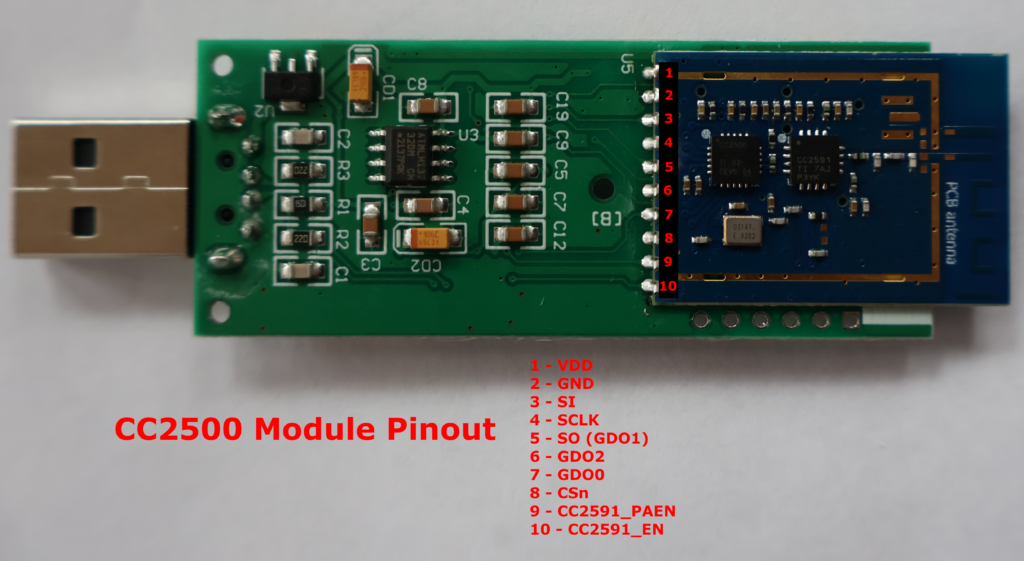
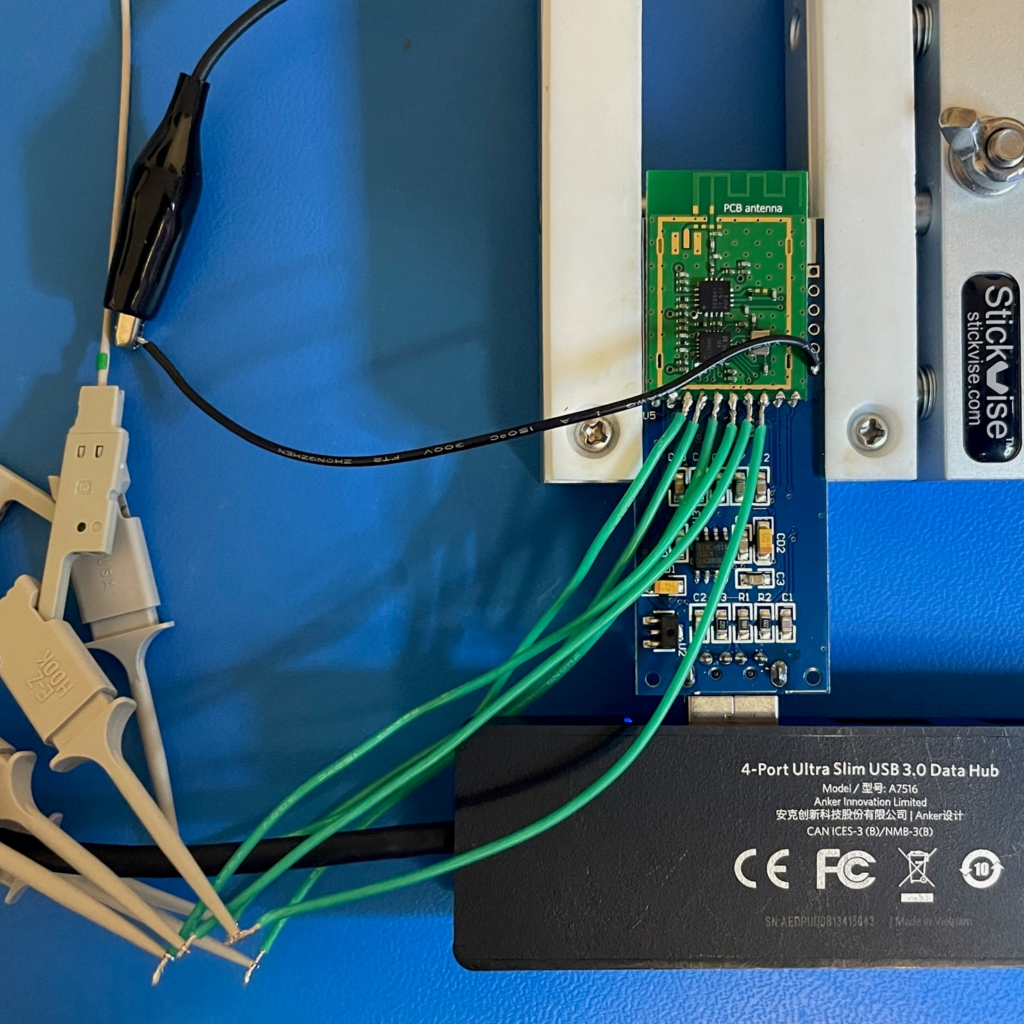
The SPI communication between the AT91SAM7X256 microcontroller and the CC2500 radio was sniffed using an oscilloscope’s logic analyzer.

M30

The M30 is a simple price optimized keypad from SunVote. The M30 just consists of two coin cell batteries, a few membrane buttons, a custom screen, an antenna, and a chip on board glob top. There are no protections preventing reading the code from the chips internal memory. It uses a Texas Instruments integrated radio/microcontroller and you can read the firmware for the 8051 microcontroller using a TI CC Debugger. Ghidra can also be used to disassemble and reverse engineer the code.
Exploitation
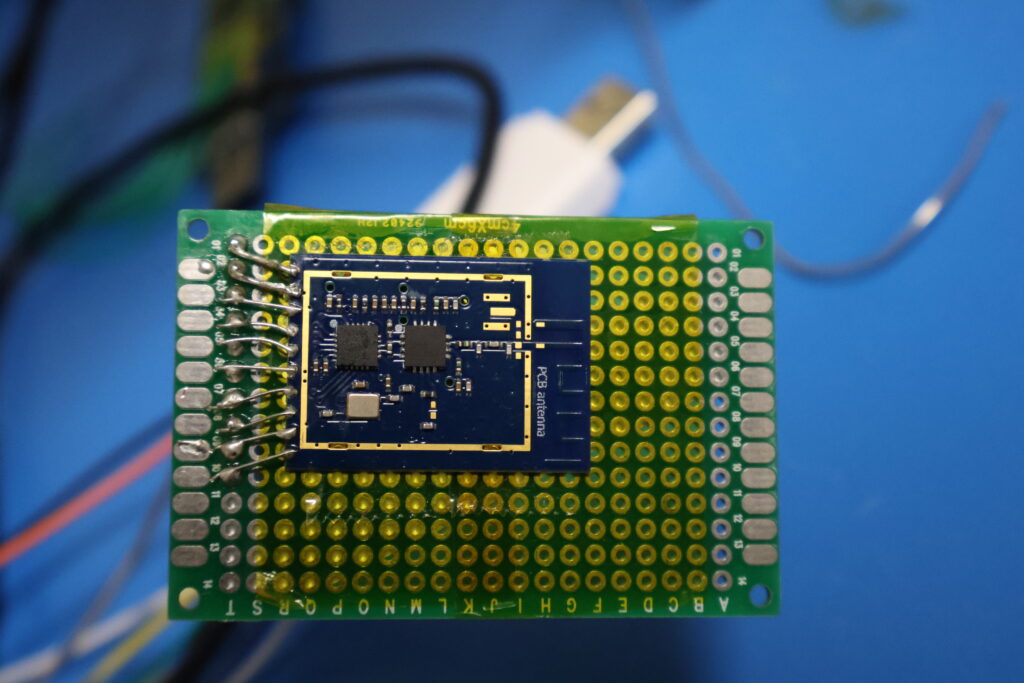
A radio daughter board was de-soldered from an EA1000 and re-purposed to send and receive radio packets. This could also have been done using the SDR, but modulating a signal from binary data to match the exact radio characteristics for transmission can be difficult. The same exact radio daughter board is also for sale on Ali Express.
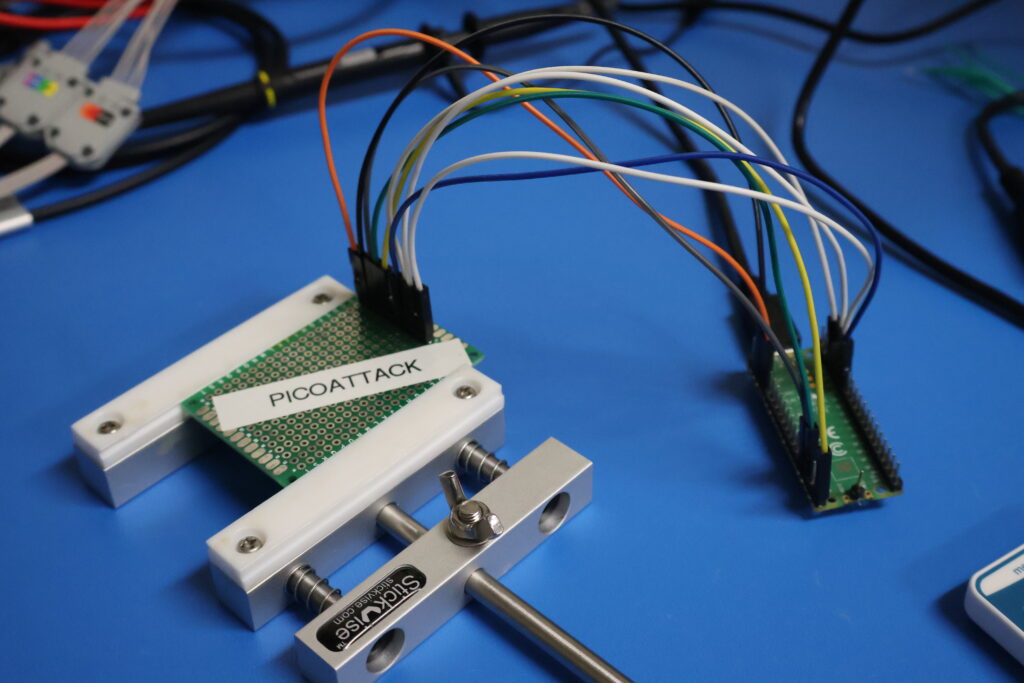
The radio daughter board was mounted and SPI was routed to a Raspberry Pi Pico (cheap microcontroller). In this configuration, the Pico could send and receive packets from the CC2500 radio. Code was written to initialize the radio and allow spoofing votes.
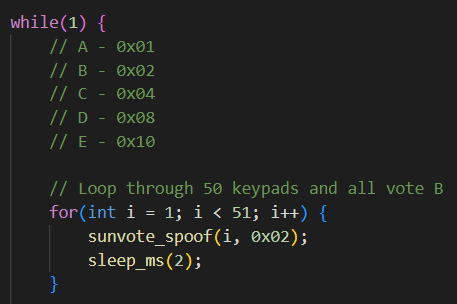
The demonstration uses presentation mode from Meridia’s EZ-VOTE software because TownVOTE is only enabled for towns. There is no difference under the hood between TownVOTE and the presentation mode, only the graphical interface is different. The code will be released in a few weeks.
Disclosure Timeline
In accordance with ethical cybersecurity practices, industry standard responsible disclosure guidelines were followed until no response was received from the vendor.
- 12/19/2022 – First email sent to Meridia with details of the vulnerability.
- 12/19/2022 – I went in person to the town manager’s office to inform them of the issue.
- 12/19/2022 – Meridia responds asking for more details on the vulnerability. They said they would give it to their security team, even though they do not have one.
- 12/19/2022 – I provided more details about the vulnerability.
- 12/20/2022 – Meridia responds talking about what the hardware/software does (off topic).
- 12/21/2022 – I respond reiterating details about the vulnerability.
- 12/22/2022 – Merida responds with a large email trying to understand the issue.
- 12/22/2022 – I respond thanking them for the in depth email and I send the video, shown in this blog, to demonstrate.
- 12/23/2022 – Meridia responds saying that they will review the information and respond appropriately.
- 12/23/2022 – I respond asking for more details on how they will fix this issue. Remember: Only SunVote can fix the issue by issuing new hardware and new software, aka a full recall. There is no software update capability on the keypads.
- No response from Meridia
- 1/5/2023 – I ask again to be informed on how they will address this issue.
- No response from Meridia
- 1/17/2023 – This blog was posted to inform the public about this issue.
At this time, it is unknown if Meridia is working with SunVote to address the issue. It is also unknown if Meridia has informed their customers.
Conclusion
The SunVote system was not designed for government voting. Meridia recently wrote on their blog that Leicester, MA decided a $91 million dollar warrant using their system. Meridia also advertises that nearly 50 towns in Massachusetts use the voting system. Overall, potentially billions of dollars in funding has been decided by this vulnerable system.
The Massachusetts state legislature should change the law to ensure town meeting voting is inherently secure. As a society, we must work together, encourage conversation, stop fighting, collaborate to solve issues, and build a better world. It is not productive when the town decides to ignore issues.
Disclaimer: The research in this post has been conducted in good faith for the common good. The author has legally purchased Meridia branded SunVote devices. This means the reverse engineering research was done on their own private property to better understand the product’s security and discover potential vulnerabilities. No town owned Meridia/SunVote devices or meetings have been impacted whatsoever.
Excellent research! Have you met with town manager yet???
Thank you! They are aware of the issue